Become Secure by Default
Find and fix broken authentication, logic bugs, and complex vulnerabilities that rules-based scanners and humans miss.
Less Noise
We save you hours on triage by prioritizing exploitable bugs that impact your users, enriched with context, proof-of-concepts, and actionable fixes.
Business Logic
We analyse code paths, developer intent, natural language rules, and IaC to uncover real risks in context.
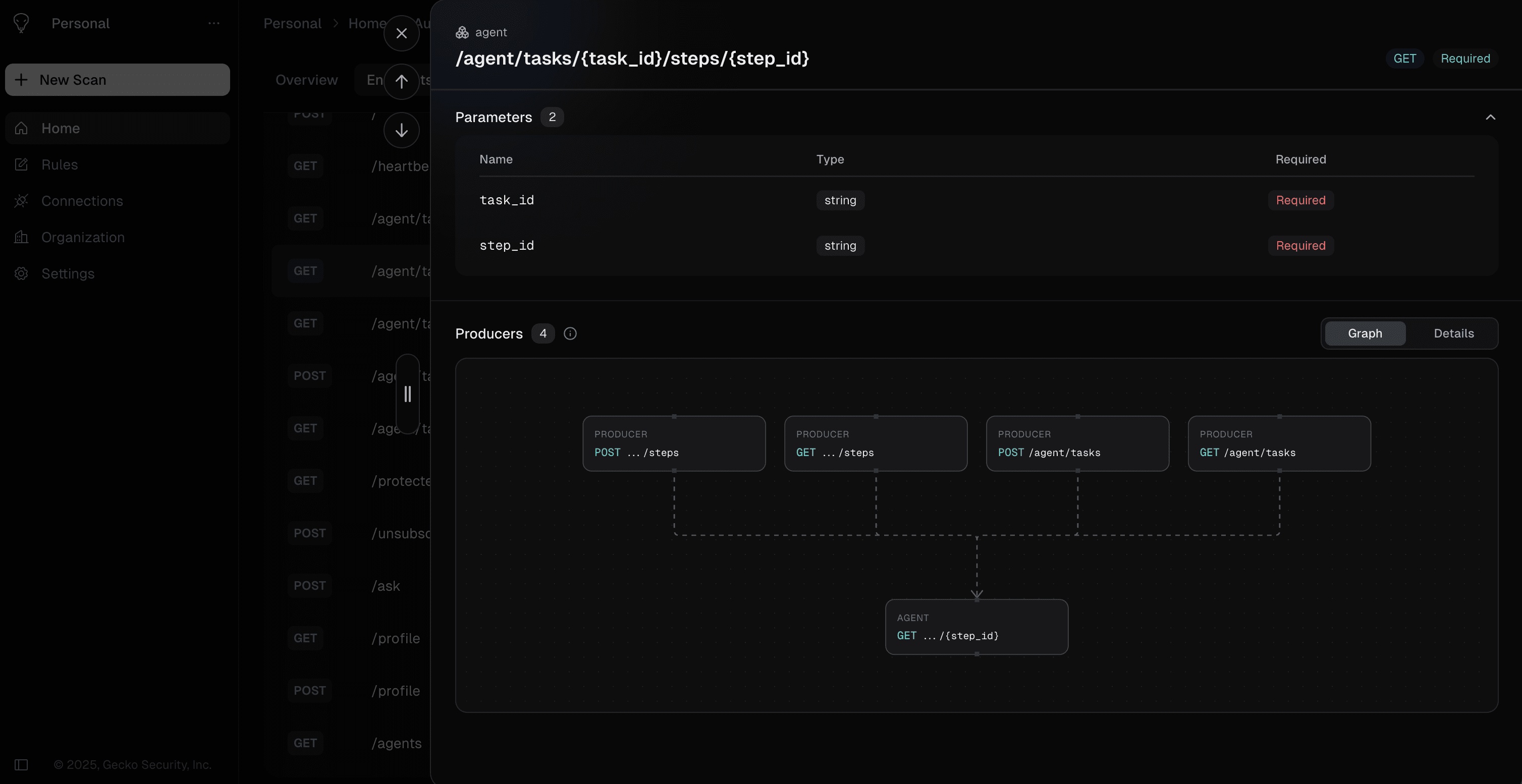
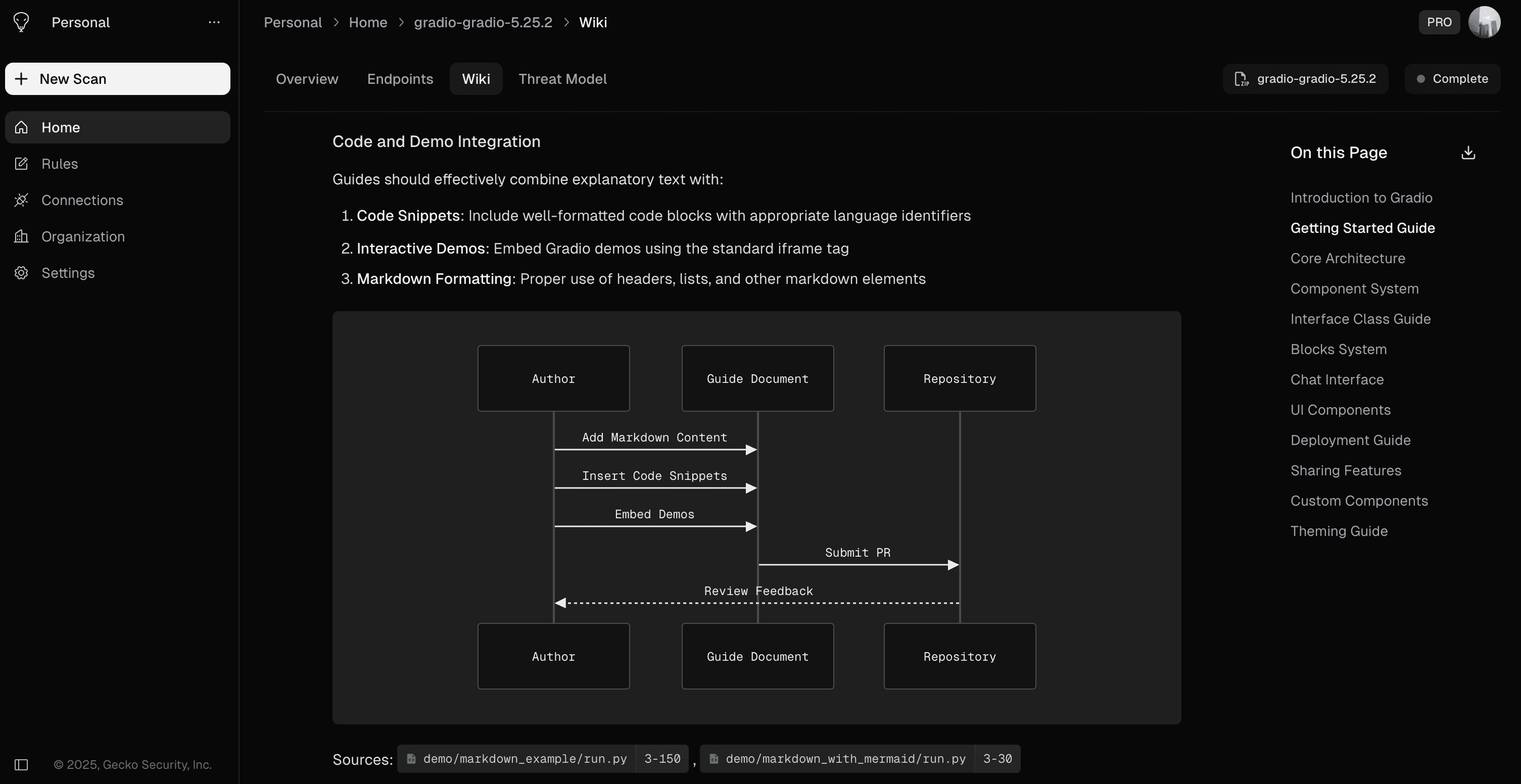
Threat Modelling
Scale threat modelling by aligning it with your business and security objectives and model targeted, exploitable attack paths.
Gecko in Action
0-Day's found and fixed by Gecko in OSS Projects.
SSRF in File Upload Processing
bentoml/BentoMLAn SSRF in the file upload processing system allows remote attackers to make arbitrary HTTP requests from the server without authentication. The vulnerability exists in the serialization/deserialization handlers for multipart form data and JSON requests, which automatically download files from user-provided URLs without proper validation of internal network addresses.
Cross-Domain Authentication Token Exposure
ollama/ollamaThe authentication flow contains a vulnerability in its model pulling mechanism. When a user pulls a model from an HTTPS server that responds with a 401 Unauthorized status, Ollama follows the WWW-Authenticate header's realm URL without validating if it belongs to the same domain as the original request. This allows an attacker to redirect the authentication flow to any domain, including registry.ollama.ai, and capture valid authentication tokens.
Authorization Bypass in Graph Execution API
Significant-Gravitas/AutoGPTThere is an authorization bypass vulnerability in the external API that allows authenticated users to access execution results from other users' graph executions. The vulnerability exists in the get_graph_execution_results endpoint, which validates that the requesting user can access the specified graph but fails to validate ownership of the execution ID parameter.
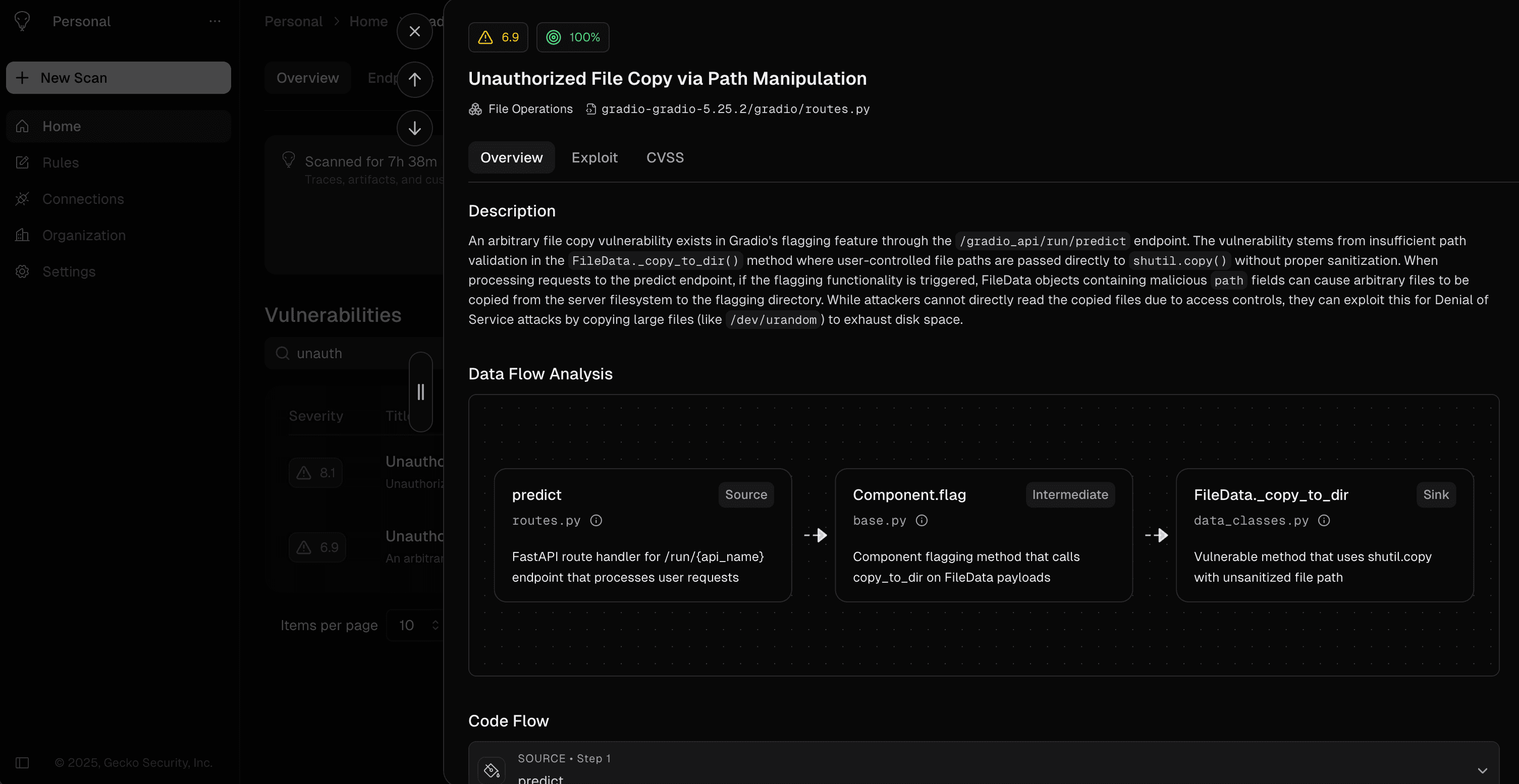
Unauthorized File Copy via Path Manipulation
gradio-app/gradioAn arbitrary file copy vulnerability in Gradio's flagging feature allows unauthenticated attackers to copy any readable file from the server's filesystem. While attackers can't read these copied files, they can cause DoS by copying large files (like /dev/urandom) to fill disk space.
SQLI CVE Bypass in Editor Execution Endpoint
eosphoros-ai/DB-GPTAn SQL injection bypasses previous fixes in the editor SQL execution functionality, allowing attackers to execute arbitrary SQL commands.
Pricing for teams of all sizes
Gecko provides enterprise-grade security scanning with flexible pricing options for teams at any scale.
Basic
Perfect for open source projects
- 10 repository scans
- Basic vulnerability scanning
- Basic PoCs and remediations
Pro
For growing teams.
- Up to 100 scans
- Advanced vulnerability scanning
- Advanced PoC's and fixes
- Teams of up to 5
- CI/CD Integration with PR/MR bot
Enterprise
For large organizations
- All Pro features plus:
- Unlimited multi-repo scanning with Custom Rules
- Automated Threat Modelling & Context Uploads
- API access and Custom Integrations
- Code Line-level Fixes
- SSO, RBAC and Audit Logs
Frequently Asked Questions
Have a question not answered here? Email us
Gecko uses an AI native engine to build a semantic understanding of your application. It links together context from your code, infrastructure and documentation to trace how data flows and trust boundaries occur. By threat modelling targeted attack scenarios, Gecko surfaces multi step and business logic vulnerabilities that pattern matching tools overlook.
Rather than using brittle AST parsing or call graph analysis, Gecko relies on semantic name bindings similar to a language server protocol. This makes its analysis more accurate, especially for microservice architecture, because it truly understands the meaning of your code and can parse dynamically typed languages. This approach leads to a lower false positive rate, of around 20 per cent based on customer testimonials and industry benchmarks, and prioritisation of remotely exploitable issues.
Yes, Gecko is built for security-conscious enterprises and supports private AI models and self-hosted deployments, ensuring security vulnerability data and source code remain completely under your control. You can request access via our Trust Center at trust.gecko.security.
